Game Engine Technology for the Enterprise
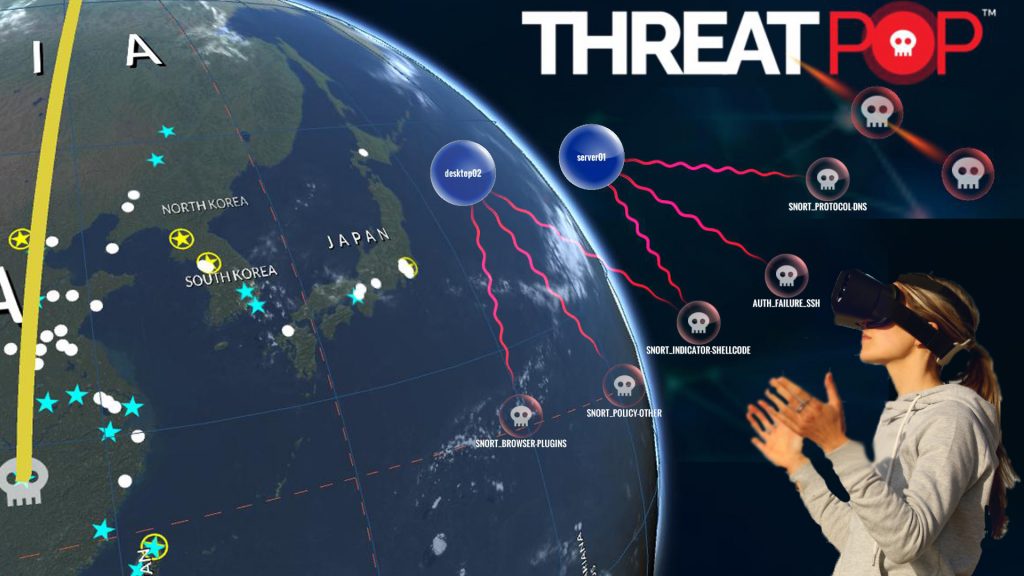
Game engine technology isn’t only for games anymore. Businesses are often seeking the best visualization and the most memorable interactive experience for customers and employees. Dovestech has been leading the charge when it comes to gamification for the enterprise, releasing its state of the art cyber security visualization product known as ThreatPop. The product offers […]
Inside the Lab: User and Entity Behavior Analytics
Members of our team have been studying existing technologies being applied in our customer environments for what is known today as User and Entity Behavior Analytics (UEBA). We have been engaged in examining the current sate of the market and studying the benefits and features claimed by new entrants into the market place. Legacy SEIM […]
Dovestech Explains: GPU Processing Power vs Passwords

Have you ever wondered how hackers are able to make quick work of leaked password databases even if the passwords are hashed? First we must discuss the basics of what a hashed password means. Cryptographic hash functions are a way to turn a text representation of data into a fixed-length “fingerprint” based on the protected […]
Online Stores Infected with Skimming Malware

Initial Estimates point to almost 6,000 online stores as victims. (October 13, 2016) Data thieves have installed scripts to skim payment card data on nearly 6,000 websites. Some of the information the malware harvest is being sent to servers in Russia. Dutch developer Willem de Groot has been investigating. Experts point out that one way […]
Google Battles State-Sponsored Cyber Attacks

A senior executive of Alphabet Inc’s Google unit said on Monday that the company was notifying customers of 4,000 state-sponsored cyber attacks per month. Speaking at a Fortune magazine tech conference in Aspen, Colorado, Google senior vice president and Alphabet board member Diane Greene mentioned the figure while touting Google’s security prowess. The internet search […]
PivotPoint Risk Analytics and Marsh Agreement

June 1, 2016 by PivotPoint Editor Marsh to integrate CyVaR into cyber risk advisory services for clients June 1, 2016 – Baltimore, MD and New York, NY –PivotPoint Risk Analytics, a leader in cyber risk analytics, and Marsh, a leading global insurance broker and risk advisor and a wholly-owned subsidiary of Marsh & McLennan Companies, […]
U.S. Cyber Command struggles to retain top cybersecurity talent

Top official in Defense Department’s cybersecurity unit says organization is doing an ‘effective job’ at recruiting, but keeping up with the evolving threat landscape remains a challenge. At U.S. Cyber Command, the top brass has made recruiting top talent a leading priority, but those efforts have been slowed by challenges in attracting and retaining the […]
The Pentagon expands program for hackers to test its security

Back in March, the US’s Department of Defense launched a “Hack the Pentagon” campaign to get hackers to test their websites and security networks for vulnerabilities, without the threat of jail time. The project was so successful that the government agency has announced it’s being expanded, including more DoD websites and networks, with further cash […]
Acer hack may have exposed 34,500 customers

Late last week, a letter surfaced detailing a data breach with Acer’s website which left customers’ credit and debit card details vulnerable, among other things. Though the time frame for the breach was stated — May 12 of last year through April 28 of this year — how many people may have been affected wasn’t […]
75% of Site Owners Cleaned Up

Google released some interesting data on hacked sites and their attempts to notify webmasters that their sites were compromised. They also released information on just how many sites are hacked – Google detected over 800,000 alone last year. Email Notifications This led to 75% of hacked sites being cleaned up when Google was able to […]