Cybersecurity and The Music Industry

Musicians need to look at cybersecurity in the same manner as they configure their personal security teams.
Our team has been called to support musicians who have been subject to ransomware attacks. Truth be told. It’s typically too late when we get the call. Paying the ransomware has consequences and risks.
CMMC-AB Standards Committee hosts the fourth Standards Podcast

Regan Edens, Chair of the CMMC-AB Standards Committee, hosts the fourth Standards Podcast. He is joined by Jeff Dalton, Chair of the Certification and Accreditation Committee. The topic of Episode 4 is scoping requirements associated with a CMMC Level 3 organiziation, looked at from an assessor’s perspective, the Organization Seeking Certification (OSC) perspective, and a […]
Ransomware Disrupts Operations at Packaging Giant WestRock

Originally Posted on Dark Reading: Incident is another reminder of how vulnerable OT environments are to attack, security experts say. Operations at $17 billion packaging firm WestRock were disrupted Saturday by a ransomware attack that impacted both its IT and operational technology (OT) networks. The attack has already caused, and will likely continue to cause, […]
IIoT World’s Manufacturing Day – March 18, 2021

ABOUT EVENT : One of a kind online conference that will bring together IIoT subject matters experts from all over the world to share insights on smart manufacturing. This virtual event will focus on deploying machine learning on devices and on the network infrastructure that supports the intelligent IoT in manufacturing. We will be gathering a […]
DovesTip 02 – What is Controlled Unclassified Information (CUI)

Has anybody seen a document marked as CUI yet? Most people would answer no. But never the less DFARS 7012/NIST 800-171 and the new Cybersecurity Maturity Model Certification are all about protection CUI. It’s how the DoD but also soon all government agencies will require verified conformance with the requirement to protect sensitive government documents, […]
DovesTip 01 – CMMC Vulnerability & Patch Management Strategies NIST 800-171

The pending inclusion of the Cyber Maturity Model Certification in the DFARS and the existing DFARS 7012 are centered on protecting controlled unclassified information (CUI). Industrial control equipped environments such as manufacturers, building developers and managers or grid suppliers for example Have more than just IT networks to contend with. Vulnerabilities in operational technology (OT) […]
Dovestech Selected for Proof of Concept Development
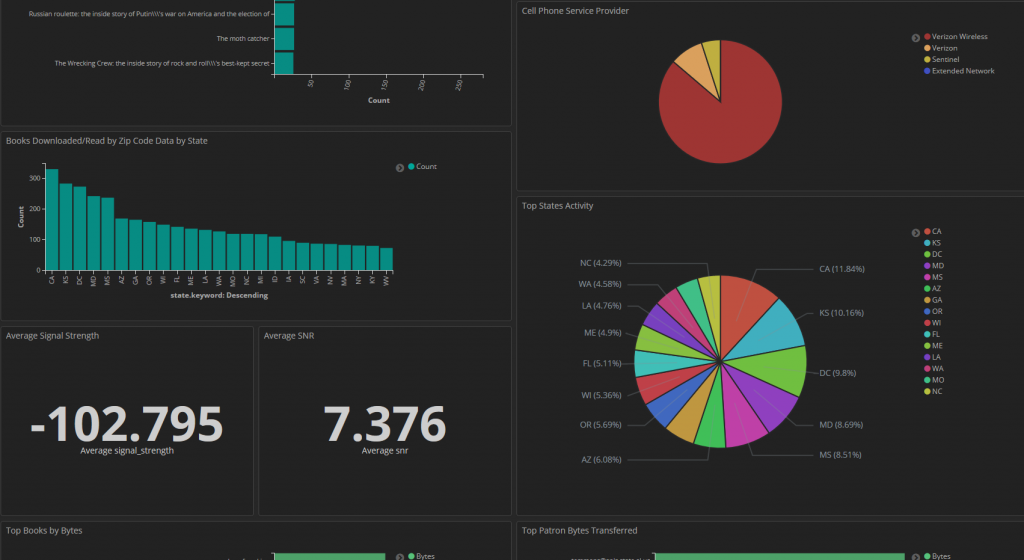
Dovestech recently was selected to exhibit our expertise and knowledge of data science for IoT analytics for a government customer. The customer sought out firms that indicated they had expertise in data analytic and visualization using ElasticSearch. Guess what? We were down selected as the top firm and we are off to the races building […]
Maryland Cyber Security Non-Profit Pushes Community Innovation and Collaboration

Maryland Cyber Security experts are growing excited about a new cyber security non-profit which is taking aim at bringing the community together for a larger impact. Maryland Innovation & Security Institute (MISI) is a non-profit formed exclusively to further and promote charitable, educational, and scientific purposes including, but not limited to, furthering innovation in cybersecurity […]
Game Engine Technology for the Enterprise
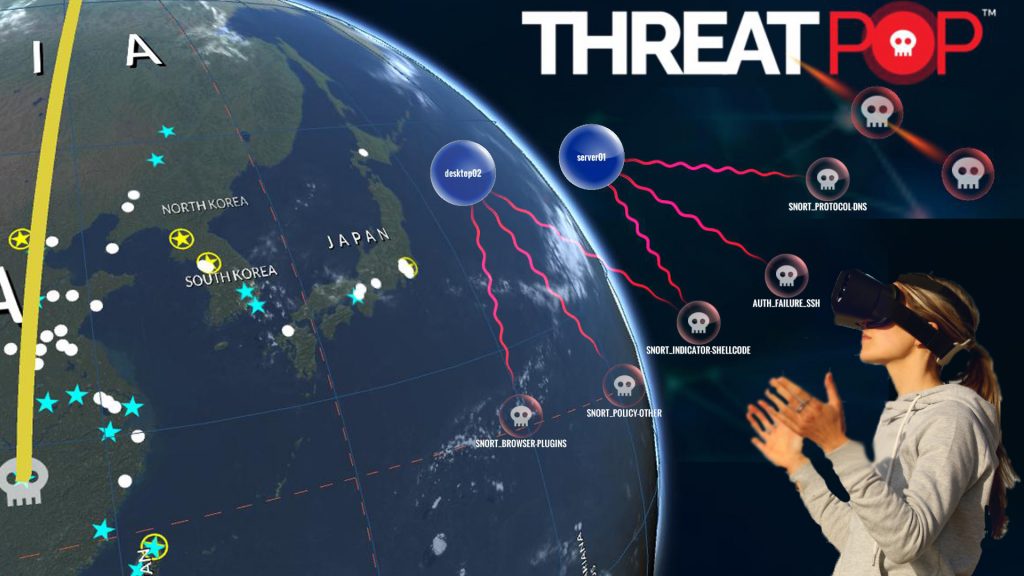
Game engine technology isn’t only for games anymore. Businesses are often seeking the best visualization and the most memorable interactive experience for customers and employees. Dovestech has been leading the charge when it comes to gamification for the enterprise, releasing its state of the art cyber security visualization product known as ThreatPop. The product offers […]
Inside the Lab: User and Entity Behavior Analytics
Members of our team have been studying existing technologies being applied in our customer environments for what is known today as User and Entity Behavior Analytics (UEBA). We have been engaged in examining the current sate of the market and studying the benefits and features claimed by new entrants into the market place. Legacy SEIM […]