
Notice: By accessing this website, you agree to our legal terms!
Dovestech specializes in developing unique solutions including Data Processing, Analytic, Virtual Reality, Augmented Reality, Gamification and Visualization solutions. We are resellers and integrators of unique malware software and managed red team solutions. We customize and implement our own proprietary patent pending cyber threat visualization and sentiment analytic tools.




Dovestech is a company comprised of highly experienced and motivated staff. We are led by veterans of the tech field but with a passion to build a different company one step at the time. This means we need every hire to fit our standards, our customer’s standards and to contribute and participate in the growth of what promises to be something different. We are seeking passionate creatives as we are not just focused on consulting and services but on building simple solutions to solve complex problems and introducing our creations into the market place. Interested? Send us your resume and please indicate the position in which you are interested. Our e-amil address is support@dovestech.com!




Cybersecurity and The Music Industry
Musicians need to look at cybersecurity in the same manner as they configure their personal security teams.
Our team has been called to support musicians who have been subject to ransomware attacks. Truth be told. It’s typically too late when we get the call. Paying the ransomware has consequences and risks.

CMMC-AB Standards Committee hosts the fourth Standards Podcast
Regan Edens, Chair of the CMMC-AB Standards Committee, hosts the fourth Standards Podcast. He is joined by Jeff Dalton, Chair of the Certification and Accreditation Committee. The topic of Episode 4 is scoping requirements associated with a CMMC Level 3 organiziation, looked at from an assessor’s perspective, the Organization Seeking Certification (OSC) perspective, and a […]

Ransomware Disrupts Operations at Packaging Giant WestRock
Originally Posted on Dark Reading: Incident is another reminder of how vulnerable OT environments are to attack, security experts say. Operations at $17 billion packaging firm WestRock were disrupted Saturday by a ransomware attack that impacted both its IT and operational technology (OT) networks. The attack has already caused, and will likely continue to cause, […]

IIoT World’s Manufacturing Day – March 18, 2021
ABOUT EVENT : One of a kind online conference that will bring together IIoT subject matters experts from all over the world to share insights on smart manufacturing. This virtual event will focus on deploying machine learning on devices and on the network infrastructure that supports the intelligent IoT in manufacturing. We will be gathering a […]

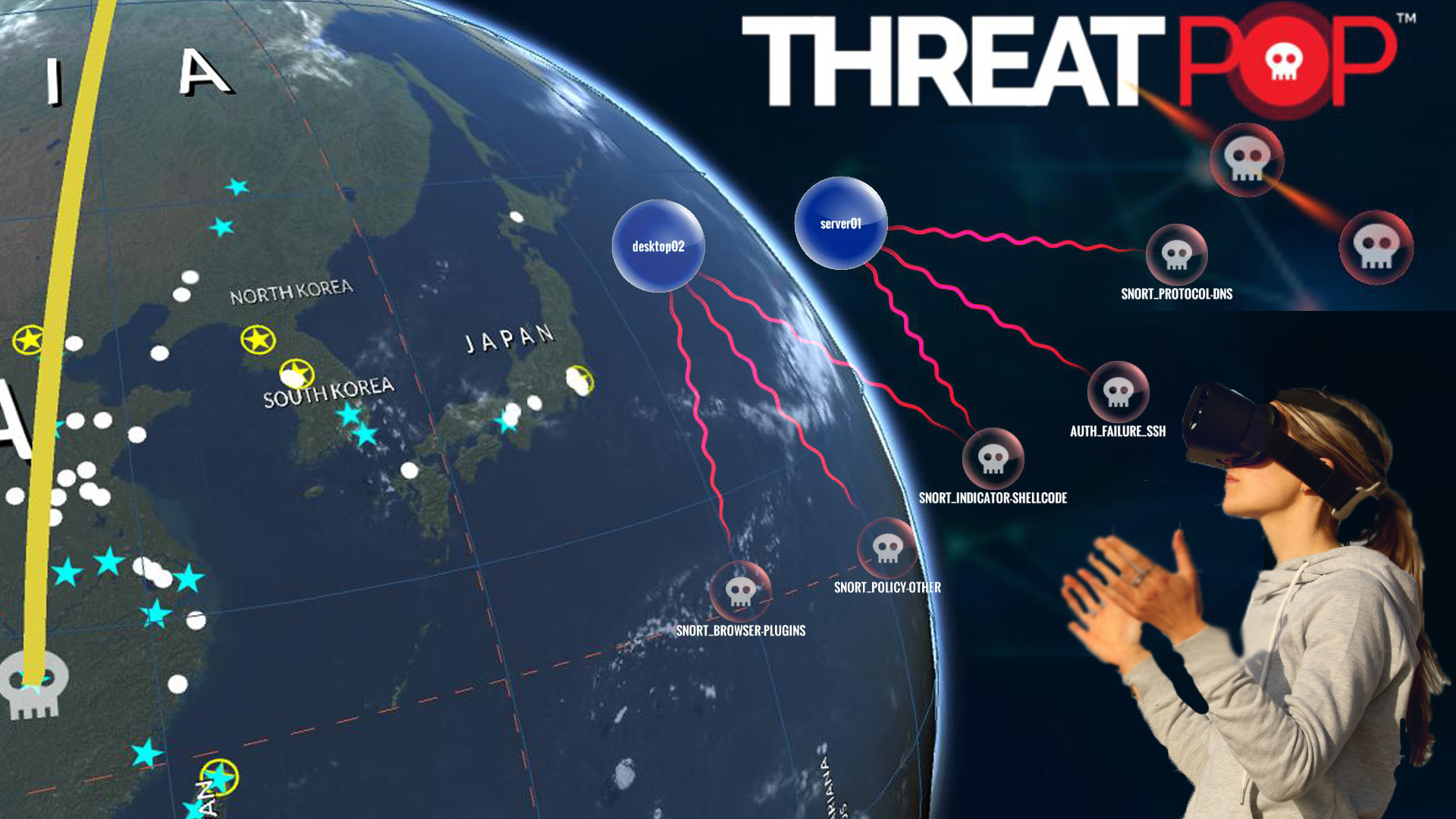
Game Engine Technology for the Enterprise
Game engine technology isn’t only for games anymore. Businesses are often seeking the best visualization and the most memorable interactive experience for customers and employees. Dovestech has been leading the charge when it comes to gamification for the enterprise, releasing its state of the art cyber security visualization product known as ThreatPop. The product offers […]
Inside the Lab: User and Entity Behavior Analytics
Members of our team have been studying existing technologies being applied in our customer environments for what is known today as User and Entity Behavior Analytics (UEBA). We have been engaged in examining the current sate of the market and studying the benefits and features claimed by new entrants into the market place. Legacy SEIM […]

Dovestech Explains: GPU Processing Power vs Passwords
Have you ever wondered how hackers are able to make quick work of leaked password databases even if the passwords are hashed? First we must discuss the basics of what a hashed password means. Cryptographic hash functions are a way to turn a text representation of data into a fixed-length “fingerprint” based on the protected […]

Online Stores Infected with Skimming Malware
Initial Estimates point to almost 6,000 online stores as victims. (October 13, 2016) Data thieves have installed scripts to skim payment card data on nearly 6,000 websites. Some of the information the malware harvest is being sent to servers in Russia. Dutch developer Willem de Groot has been investigating. Experts point out that one way […]






